Vulnerability scanning tools are essential for identifying and mitigating security risks in today’s digital landscape. These tools automate the process of scanning systems and applications for known vulnerabilities, providing valuable insights to strengthen your cybersecurity posture.
Understanding Vulnerability Scanning Tools
Vulnerability scanning tools work by probing systems and applications for known weaknesses. They compare the scanned environment against a database of known vulnerabilities, flagging any potential security holes. These tools provide a comprehensive overview of your security posture, highlighting areas that require immediate attention.
Types of Vuln Scanning Tools
Various types of vulnerability scanning tools cater to different needs:
- Network Vulnerability Scanners: These tools identify vulnerabilities in network devices, such as routers, firewalls, and servers.
- Web Application Scanners: Specifically designed to uncover vulnerabilities in web applications, such as cross-site scripting (XSS) and SQL injection flaws.
- Database Scanners: Focus on identifying security weaknesses in databases, protecting sensitive data from unauthorized access.
- Host-Based Scanners: Installed on individual systems to scan for vulnerabilities locally, providing a detailed analysis of the host’s security posture.
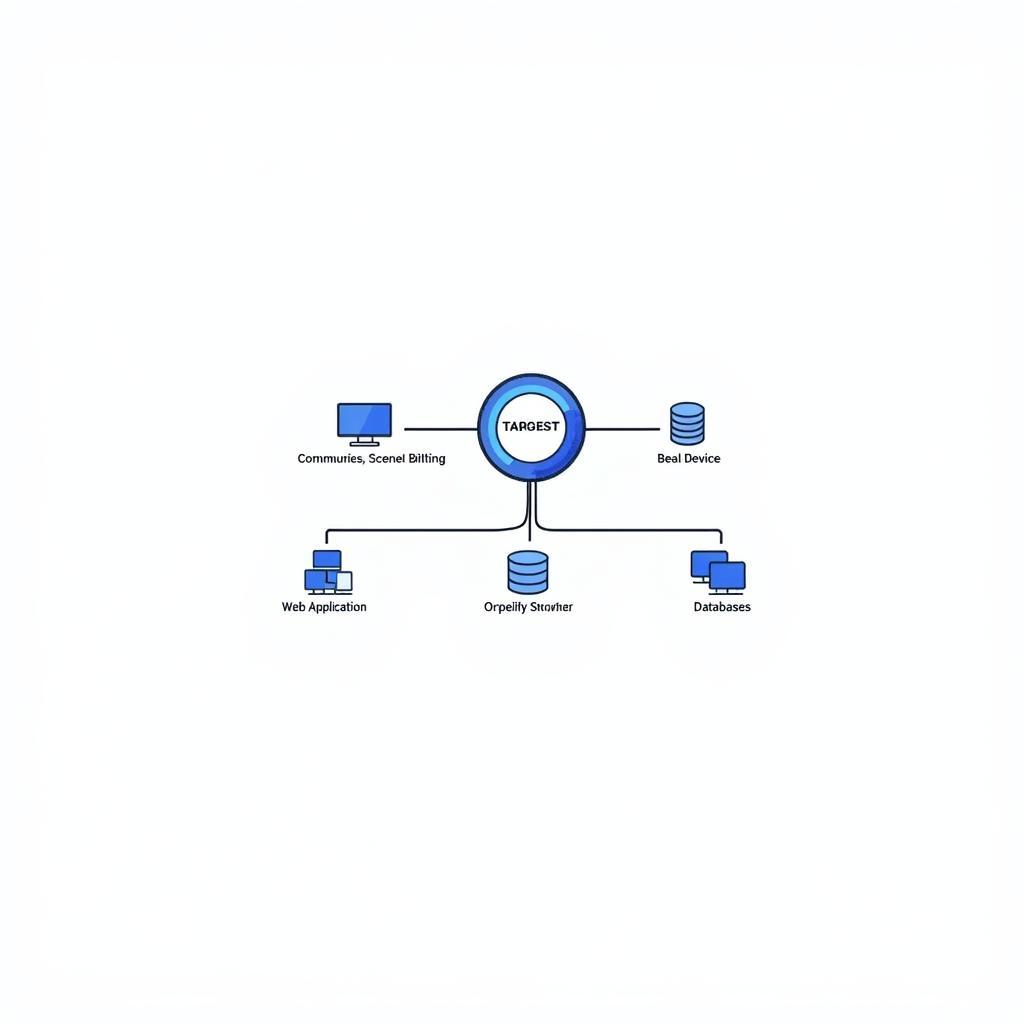 Different Types of Vulnerability Scanning Tools
Different Types of Vulnerability Scanning Tools
Why are Vuln Scanning Tools Important?
Vulnerability scanning tools offer numerous benefits:
- Proactive Security: Identify vulnerabilities before attackers can exploit them, proactively mitigating risks.
- Reduced Attack Surface: Help minimize the attack surface by uncovering and addressing security weaknesses.
- Compliance Requirements: Assist organizations in meeting regulatory compliance requirements by identifying and remediating vulnerabilities.
- Cost Savings: Proactive vulnerability management helps avoid costly data breaches and system downtime.
Key Features of Effective Vulnerability Scanning Tools
When choosing Vuln Scanning Tools, consider the following features:
- Comprehensive Vulnerability Database: Regularly updated database with the latest known vulnerabilities.
- Accuracy and Low False Positives: Reliable scanning engine that minimizes false positives, saving time and effort.
- Detailed Reporting and Remediation Guidance: Clear and concise reports with actionable remediation steps.
- Integration Capabilities: Seamless integration with other security tools for streamlined workflows.
Choosing the Right Vuln Scanning Tools
Selecting the right vulnerability scanning tools depends on your specific needs:
- Network Infrastructure: For scanning network devices, consider tools like network vulnerability scanning tools free.
- Software Development Lifecycle: Integrate ci cd vulnerability scanning tools into your development pipeline for continuous security testing.
- Open-Source Options: Explore tools used for vulnerability scanning that align with your budget and technical expertise.
“Regular vulnerability scanning is not just a security best practice, it’s a necessity in today’s threat landscape,” says John Smith, a Cybersecurity Expert at SecureTech Solutions. “Organizations need to prioritize vulnerability management to stay ahead of emerging threats and protect their valuable assets.”
Best Practices for Effective Vulnerability Scanning
To maximize the effectiveness of vuln scanning tools:
- Establish a Regular Scanning Schedule: Conduct scans frequently to identify and address vulnerabilities promptly.
- Prioritize Remediation Efforts: Focus on remediating critical vulnerabilities first, based on their potential impact.
- Stay Updated: Keep your scanning tools and vulnerability databases up-to-date for accurate results.
- Combine with Penetration Testing: Supplement vulnerability scanning with penetration testing for a more comprehensive security assessment.
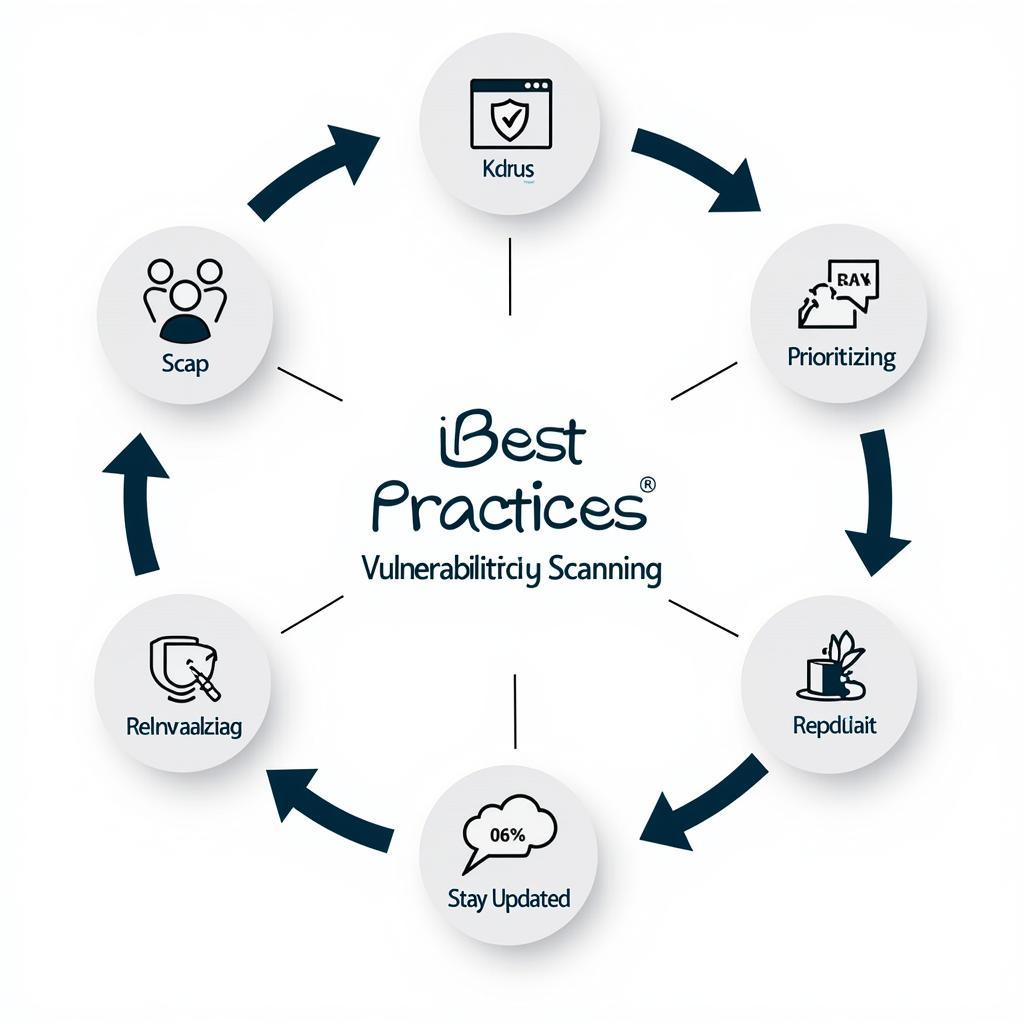 Best Practices for Effective Vulnerability Scanning
Best Practices for Effective Vulnerability Scanning
Conclusion
Vulnerability scanning tools are indispensable for maintaining a robust cybersecurity posture. By proactively identifying and addressing security weaknesses, organizations can effectively mitigate risks, protect their assets, and ensure business continuity. For expert guidance on implementing and optimizing your vulnerability management program, contact CARW Workshop at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States.





2 Responses