In the increasingly complex world of automotive electronics, identifying and mitigating vulnerabilities is paramount. Tool Supports Vulnerability Scanning plays a crucial role in safeguarding vehicle systems from potential cyber threats and ensuring operational safety. This article delves into the importance of vulnerability scanning tools, their application in automotive diagnostics, and how they empower technicians and repair shops to stay ahead of emerging security challenges.
Automotive systems are becoming more interconnected and reliant on software, increasing their exposure to cyberattacks. These attacks can compromise various vehicle functions, from infotainment systems to critical safety features. Using tools that support vulnerability scanning allows technicians to proactively identify weaknesses in these systems before they can be exploited. This is a significant advancement in automotive diagnostics, moving beyond traditional mechanical troubleshooting. automated code scanning tools can also be used in this context.
Why Use Tool Supports Vulnerability Scanning?
Modern vehicles are essentially computers on wheels, with complex electronic control units (ECUs) managing everything from engine performance to braking systems. Each ECU runs software that can potentially contain vulnerabilities. os scanning tools can play a critical role in ensuring the overall security of the vehicle’s operating system.
- Proactive Security: Vulnerability scanning allows for the early detection of security flaws, preventing potential exploits.
- Enhanced Safety: By addressing vulnerabilities, you contribute to the overall safety and reliability of the vehicle.
- Compliance: Regular vulnerability scanning helps meet emerging industry standards and regulations related to automotive cybersecurity.
- Reduced Costs: Addressing vulnerabilities proactively can prevent costly repairs and downtime associated with successful cyberattacks.
How to Effectively Utilize Vulnerability Scanning Tools
Using vulnerability scanning tools effectively requires a structured approach. Here’s a step-by-step guide:
- Choose the Right Tool: Select a tool that is compatible with the vehicle’s make, model, and systems.
- Connect to the Vehicle: Establish a secure connection between the scanning tool and the vehicle’s diagnostic port (OBD-II).
- Initiate the Scan: Start the scanning process, ensuring that all relevant ECUs are included.
- Analyze the Results: Carefully review the scan report, paying attention to the severity of identified vulnerabilities. how to scan plugins pro tools may offer some parallels in terms of analysis and remediation.
- Develop a Remediation Plan: Create a plan to address the identified vulnerabilities, which may involve software updates or other corrective actions.
- Document Everything: Maintain detailed records of the scanning process, identified vulnerabilities, and remediation steps taken.
“Regular vulnerability scanning is no longer optional; it’s a necessity in today’s connected car landscape. Ignoring these risks can have severe consequences,” warns John Miller, Senior Automotive Cybersecurity Consultant at SecureAuto Solutions.
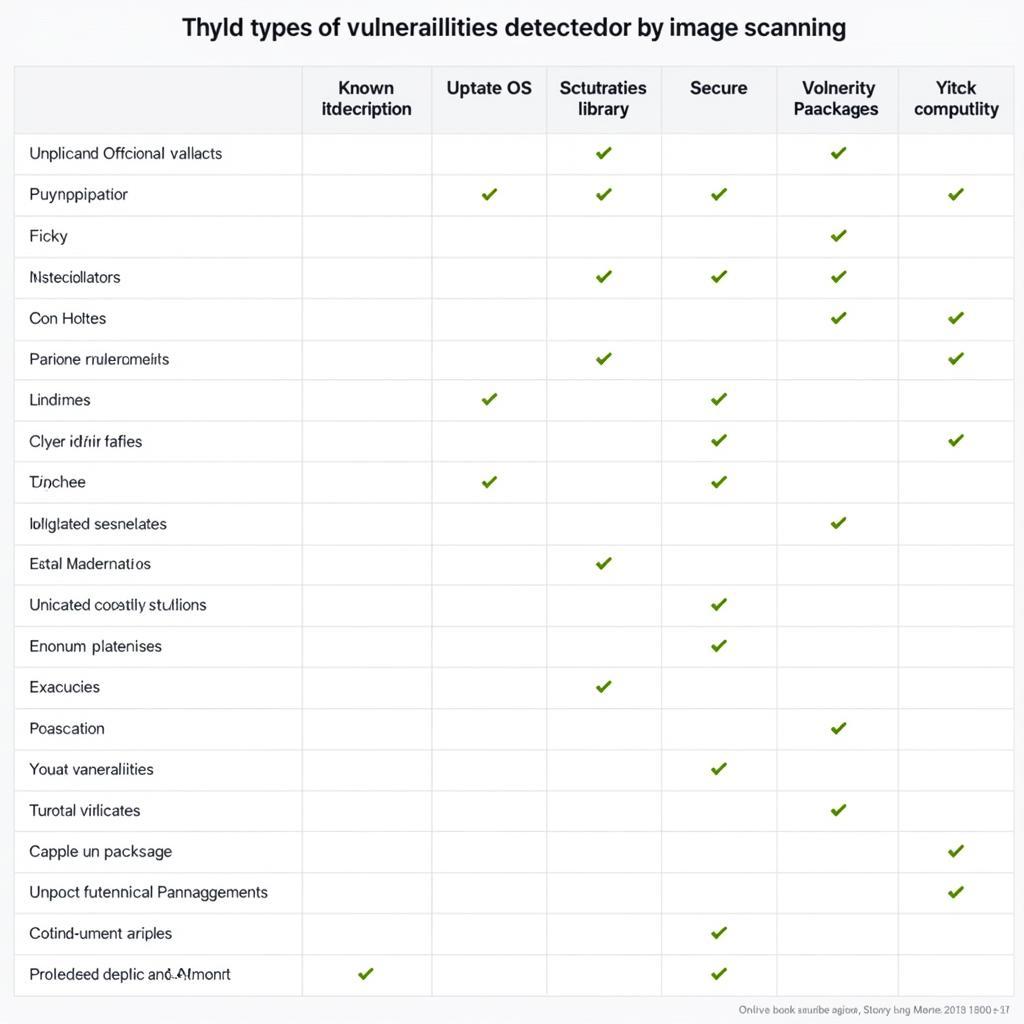
What are the Common Types of Automotive Vulnerabilities?
Understanding the common types of automotive vulnerabilities is essential for effective mitigation. These can include:
- Software Bugs: Errors in the software code that can be exploited by attackers.
- Weak Authentication: Inadequate security measures that allow unauthorized access to vehicle systems.
- Lack of Encryption: Unencrypted communication channels that expose sensitive data to interception.
- Insecure Firmware Updates: Vulnerabilities in the firmware update process that can be exploited to install malicious code.
- Insufficient Input Validation: Failure to properly validate user inputs, allowing attackers to inject malicious code. distributed scanning tools can be particularly useful in identifying these vulnerabilities across a fleet of vehicles.
“Staying informed about the latest vulnerability trends is crucial. Automotive cybersecurity is a constantly evolving field, and new threats emerge regularly,” adds Maria Sanchez, Lead Security Researcher at AutoSec Technologies.
Conclusion
Tool supports vulnerability scanning is a critical component of modern automotive diagnostics and security. By proactively identifying and addressing vulnerabilities, technicians and repair shops can ensure the safety, reliability, and security of vehicles in an increasingly connected world. wp scan tool demonstrates the importance of scanning for vulnerabilities, even in seemingly unrelated systems, highlighting the pervasive nature of cybersecurity concerns. Don’t hesitate to connect with CARW Workshop at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States for expert support and guidance.