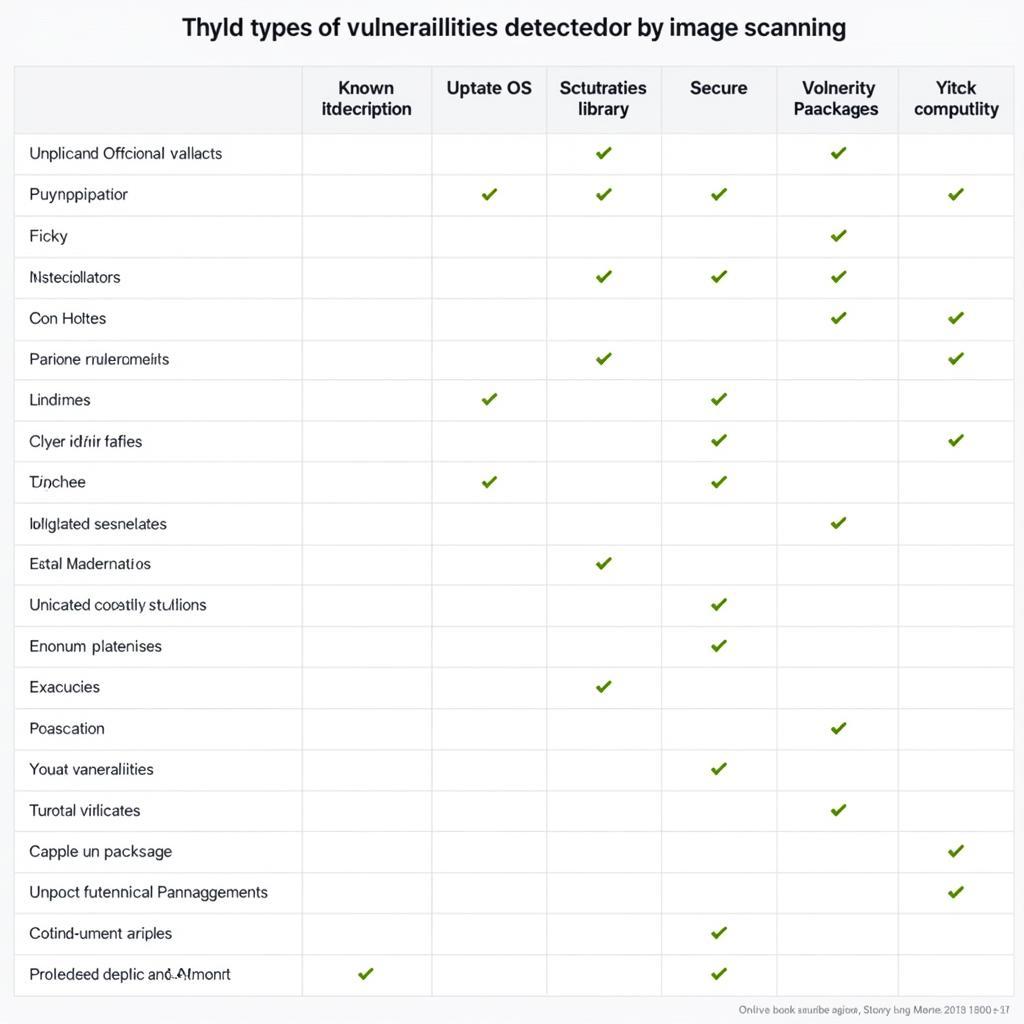
Nessus Scanning Tool Vulnerabilities are a crucial aspect of cybersecurity in today’s digital landscape. Understanding how Nessus identifies vulnerabilities and how to interpret its findings is essential for maintaining a robust security posture. This comprehensive guide will explore the intricacies of Nessus, its capabilities in uncovering vulnerabilities, and best practices for utilizing this powerful tool.
What Makes Nessus a Leading Vulnerability Scanner?
Nessus is renowned for its comprehensive vulnerability database, regularly updated with the latest threats and exploits. Its powerful scanning engine can identify a wide range of vulnerabilities, from misconfigurations and outdated software to more complex security flaws. secrets scanning tool But what sets Nessus apart is its ability to not just pinpoint vulnerabilities, but also provide actionable insights for remediation. Think of it as a digital detective, meticulously examining your systems for weaknesses and providing you with a detailed report of its findings.
This proactive approach allows organizations to address vulnerabilities before they can be exploited by malicious actors. Nessus provides detailed reports outlining the severity of each vulnerability, along with recommended mitigation steps. This information empowers security teams to prioritize their efforts and efficiently address the most critical threats.
Understanding Nessus Scanning Tool Vulnerabilities: A Step-by-Step Guide
Utilizing Nessus effectively involves a systematic approach. First, define the scope of your scan, specifying the target systems or networks. Next, choose the appropriate scan template based on your specific needs and the type of vulnerabilities you’re looking for. Once the scan is complete, analyze the results, paying close attention to the severity levels assigned to each vulnerability.
Finally, develop and implement a remediation plan to address the identified vulnerabilities. This iterative process ensures continuous improvement in your security posture.
Interpreting Nessus Scan Results: Decoding the Findings
Nessus scan results can sometimes seem overwhelming, especially for those new to the tool. However, understanding the structure and terminology used in the reports is key to effectively addressing the identified vulnerabilities. Each vulnerability is assigned a severity level, ranging from critical to low, which indicates the potential impact of the flaw.
The report also provides detailed information about the vulnerability, including its description, potential impact, and recommended remediation steps. Don’t be intimidated by the technical jargon. Focus on understanding the severity levels and the recommended actions.
[what is the most widely used port scanning tool](https://carw.store/what-is-the most-widely-used-port-scanning-tool/)
Best Practices for Using Nessus: Maximizing its Potential
To get the most out of Nessus, consider these best practices: regularly update the plugin database to ensure you’re detecting the latest threats, customize scan templates to target specific vulnerabilities relevant to your environment, and schedule regular scans to maintain a proactive security posture.
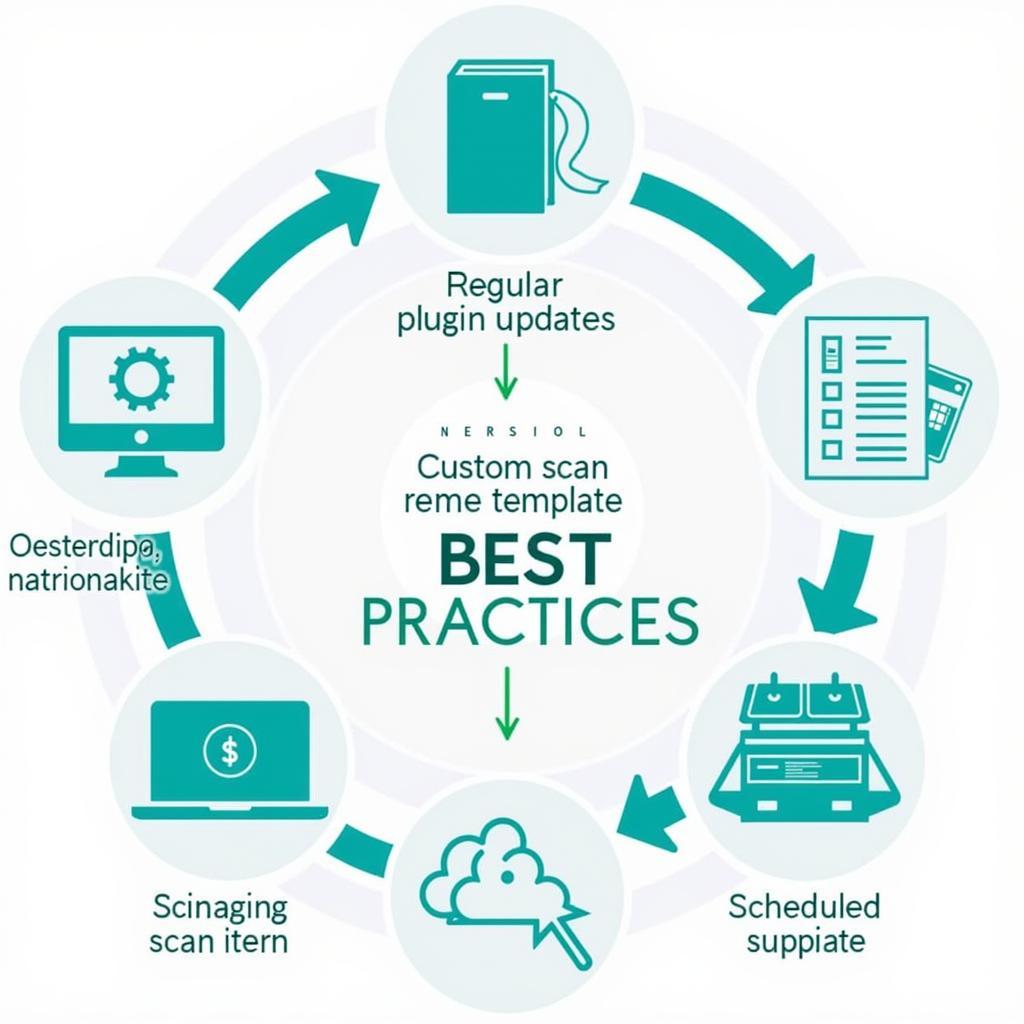 Nessus Best Practices
Nessus Best Practices
Also, integrate Nessus with other security tools to streamline your workflow and enhance your overall security posture. Remember, consistent and informed use of Nessus is crucial for staying ahead of evolving cyber threats.
Why Regular Nessus Scans Are Crucial
Regular Nessus scans are vital for maintaining a strong security posture. Think of it like regular health checkups. Just as regular checkups help identify potential health issues early on, regular Nessus scans help identify vulnerabilities before they can be exploited.
openvas as a scap scan tool This proactive approach minimizes the risk of security breaches and data leaks, safeguarding your organization’s valuable assets.
“Regular vulnerability scanning with a tool like Nessus is no longer a luxury, it’s a necessity,” says John Smith, Cybersecurity Expert at SecureTech Solutions. “The threat landscape is constantly evolving, and staying ahead of the curve requires constant vigilance.”
Integrating Nessus into Your Security Workflow
Integrating Nessus into your existing security workflow can significantly enhance your overall security posture. This integration allows for seamless vulnerability management, automated reporting, and efficient remediation. By connecting Nessus with other security tools, you can create a centralized security hub that provides a comprehensive view of your organization’s security landscape.
qualys web application scanning tool This holistic approach enables faster incident response, improved threat detection, and a more proactive security strategy.
“Integrating Nessus with other security tools is like building a fortress around your data,” adds Jane Doe, Senior Security Analyst at CyberShield Inc. “Each tool plays a vital role in strengthening your defenses and protecting against potential threats.”
microsoft access scanning tool
Conclusion
Nessus scanning tool vulnerabilities are a critical aspect of modern cybersecurity. Understanding how Nessus identifies these vulnerabilities and how to effectively interpret its findings is crucial for maintaining a robust security posture. By implementing the best practices outlined in this guide and integrating Nessus into your security workflow, you can proactively address vulnerabilities and stay ahead of evolving cyber threats. For personalized assistance and tailored solutions, connect with us at CARW Workshop. Call us at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States. We are here to help you navigate the complexities of Nessus and empower you to build a more secure digital environment.