The Log4Shell vulnerability sent shockwaves through the digital world, and the automotive industry wasn’t immune. Using a reliable Log4shell Scan Tool is crucial for identifying and mitigating this critical vulnerability within your vehicle’s software systems. This article will guide you through the process of understanding, identifying, and addressing Log4Shell, ensuring your automotive systems remain secure.
Understanding the Log4Shell Vulnerability in Automotive Systems
Log4Shell, officially known as CVE-2021-44228, exploits a flaw in the widely used Java logging library, Log4j. This vulnerability allows attackers to remotely execute malicious code, potentially compromising sensitive data and controlling vehicle functions. While many might think of Log4j as primarily a server-side concern, it’s increasingly integrated into automotive software, including infotainment systems, telematics, and even some safety-critical components. This makes a thorough log4shell scan tool indispensable.
Why is Log4Shell a Threat to Vehicles?
The interconnected nature of modern vehicles creates a complex attack surface. A successful Log4Shell exploit could lead to various damaging outcomes, from data breaches and vehicle theft to manipulating critical systems like brakes and steering. Imagine the chaos if a malicious actor could remotely disable a fleet of vehicles. This highlights the importance of using a log4shell scan tool to proactively protect your automotive systems.
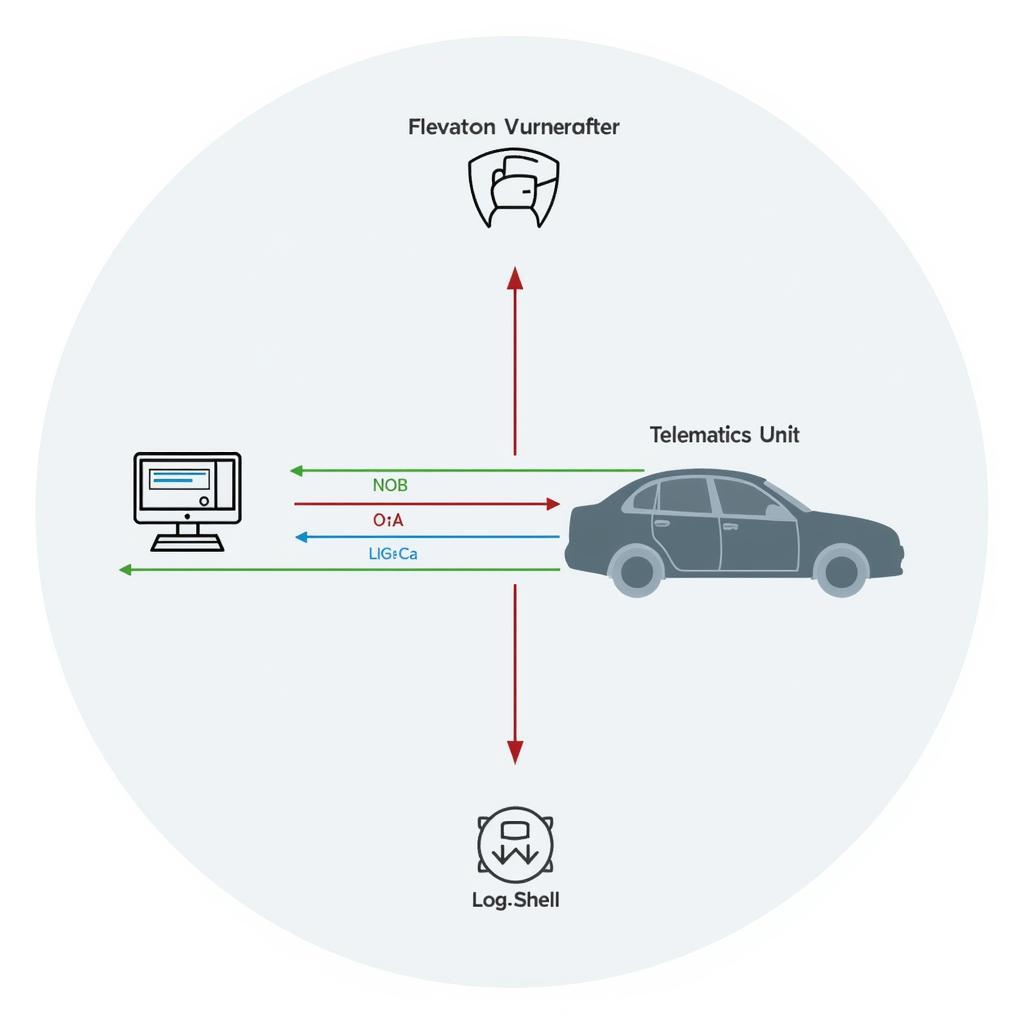 Log4Shell Vulnerability in Car Systems
Log4Shell Vulnerability in Car Systems
Selecting the Right Log4Shell Scan Tool
Choosing an appropriate log4shell scan tool is the first step towards securing your systems. Not all tools are created equal; some are designed for general-purpose scanning, while others are specifically tailored for embedded systems like those found in vehicles. Look for tools that:
- Support embedded systems: Ensure the tool can effectively scan the specific hardware and software configurations present in automotive environments.
- Provide deep scanning capabilities: The tool should be able to analyze various file formats and communication protocols commonly used in vehicles.
- Offer remediation guidance: A good tool will not only identify vulnerabilities but also provide actionable steps for mitigation.
- Generate detailed reports: Comprehensive reporting helps document the scanning process and track remediation efforts.
Key Features to Look for in a Log4Shell Scan Tool
Beyond the basic functionalities, certain features can enhance the effectiveness of a log4shell scan tool:
- Real-time monitoring: Continuous monitoring allows for immediate detection of new vulnerabilities as they emerge.
- Integration with existing security tools: Seamless integration streamlines the vulnerability management process.
- Customizable scanning rules: Tailor the tool to your specific environment and security policies.
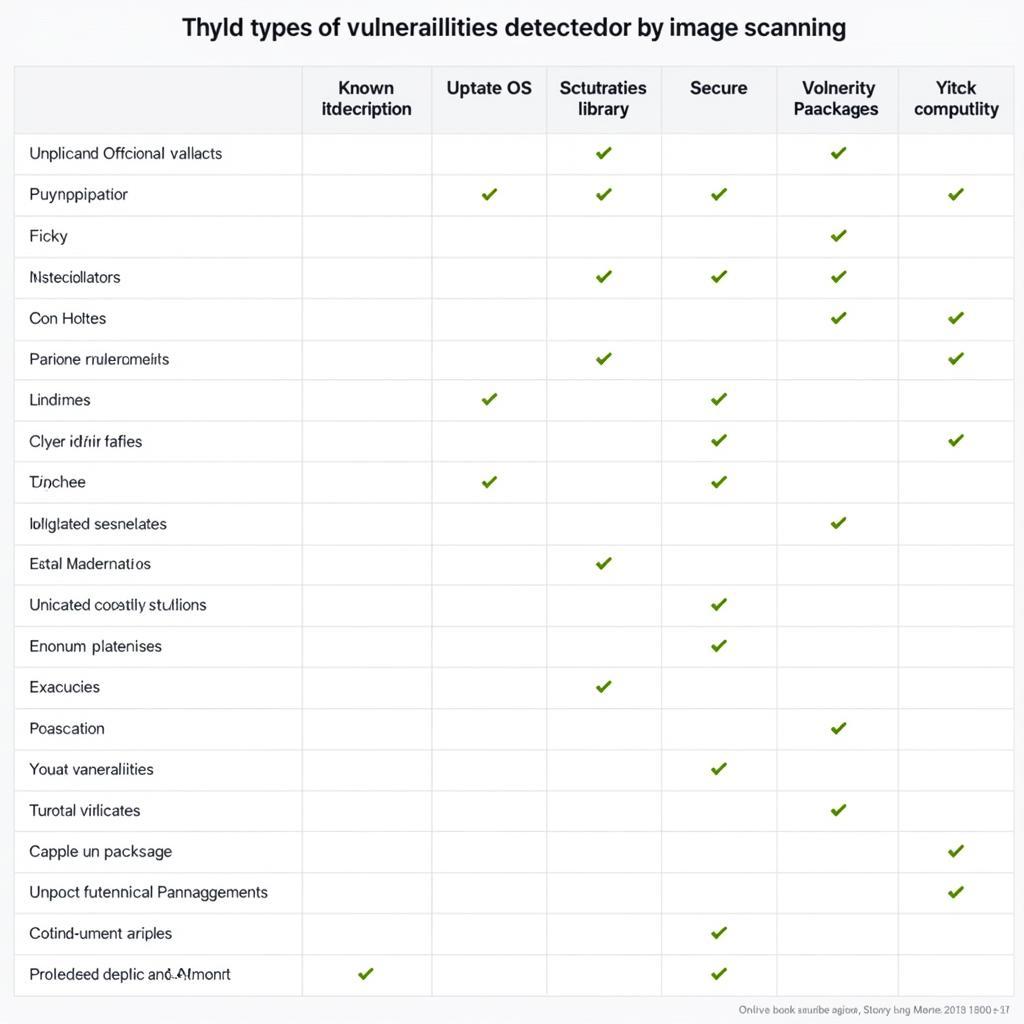
 Key Features of Log4Shell Scan Tools
Key Features of Log4Shell Scan Tools
Implementing a Log4Shell Scan and Remediation Strategy
Using a log4shell scan tool is just one piece of the puzzle. A comprehensive strategy involves:
- Inventory your systems: Identify all systems and components that utilize Log4j.
- Perform regular scans: Schedule recurring scans to detect new vulnerabilities promptly.
- Prioritize remediation: Address critical vulnerabilities first based on their potential impact.
- Implement patches and updates: Apply recommended patches and updates from vendors.
- Validate remediation efforts: Re-scan systems after applying patches to ensure effectiveness.
Best Practices for Log4Shell Remediation in Automotive
Remediation within automotive systems can be complex due to the intricate nature of the embedded software. Consider these best practices:
- Collaborate with vendors: Work closely with vehicle manufacturers and software suppliers to obtain specific remediation guidance.
- Test thoroughly: Rigorous testing is essential before deploying patches to ensure they don’t introduce new issues.
- Maintain detailed records: Document all scanning and remediation activities for auditing and compliance purposes.
“Addressing Log4Shell effectively requires a proactive approach. Regular scanning and prompt patching are crucial for minimizing the risk,” says John Smith, Senior Cybersecurity Engineer at AutoSec Solutions.
Conclusion
The Log4Shell vulnerability poses a significant threat to the automotive industry. Using a robust log4shell scan tool, combined with a well-defined remediation strategy, is paramount to protecting vehicle systems from this critical vulnerability. By taking proactive steps, we can ensure the safety and security of our increasingly connected vehicles. Don’t hesitate to reach out to us at CARW Workshop for assistance. Call us at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States.
“Ignoring Log4Shell is not an option. The potential consequences are simply too high, especially in the automotive sector,” warns Jane Doe, Lead Automotive Security Consultant at SecureCar Systems.