Automotive cybersecurity is no longer a futuristic concern; it’s a present-day reality. With vehicles becoming increasingly reliant on software and interconnected systems, the risk of cyberattacks is higher than ever. Dod Vulnerability Scanning Tools are essential for identifying and mitigating these risks, ensuring the safety and security of modern vehicles.
Understanding the Importance of DOD Vulnerability Scanning Tools
The Department of Defense (DOD) has established stringent cybersecurity standards, recognizing the potential vulnerabilities in connected systems, including those in vehicles. DOD vulnerability scanning tools are designed to identify weaknesses in software, hardware, and network configurations that could be exploited by malicious actors. These tools are crucial for automotive manufacturers, repair shops, and even individual vehicle owners who are serious about cybersecurity.
Why Use DOD Vulnerability Scanning Tools in Automotive Applications?
The automotive industry is increasingly adopting connected car technologies, leading to a surge in potential entry points for cyberattacks. Everything from the infotainment system to the engine control unit (ECU) can be a target. DOD vulnerability scanning tools help pinpoint these vulnerabilities before they can be exploited.
- Identify Security Gaps: These tools thoroughly scan vehicle systems, identifying weaknesses in software code, network protocols, and hardware configurations.
- Mitigate Risks: By identifying vulnerabilities, these tools allow manufacturers and repair shops to implement appropriate security measures to mitigate the risk of cyberattacks.
- Ensure Compliance: Using DOD-approved tools can help ensure compliance with industry regulations and cybersecurity best practices.
- Enhance Safety and Security: Protecting vehicles from cyber threats is essential for ensuring the safety of drivers and passengers.
 DOD Vulnerability Scanning Tool In Action
DOD Vulnerability Scanning Tool In Action
Choosing the Right DOD Vulnerability Scanning Tool
Selecting the appropriate DOD vulnerability scanning tool requires careful consideration of several factors.
Key Features to Look For:
- Comprehensive Coverage: The tool should be capable of scanning a wide range of vehicle systems and communication protocols.
- Regular Updates: Cybersecurity threats are constantly evolving, so the tool must receive regular updates to stay ahead of emerging vulnerabilities.
- Ease of Use: The tool should be user-friendly and intuitive, even for those without extensive cybersecurity expertise.
- Detailed Reporting: The tool should provide comprehensive reports that clearly identify vulnerabilities and offer remediation recommendations.
- Integration with Existing Systems: Ideally, the tool should integrate seamlessly with existing diagnostic and repair equipment.
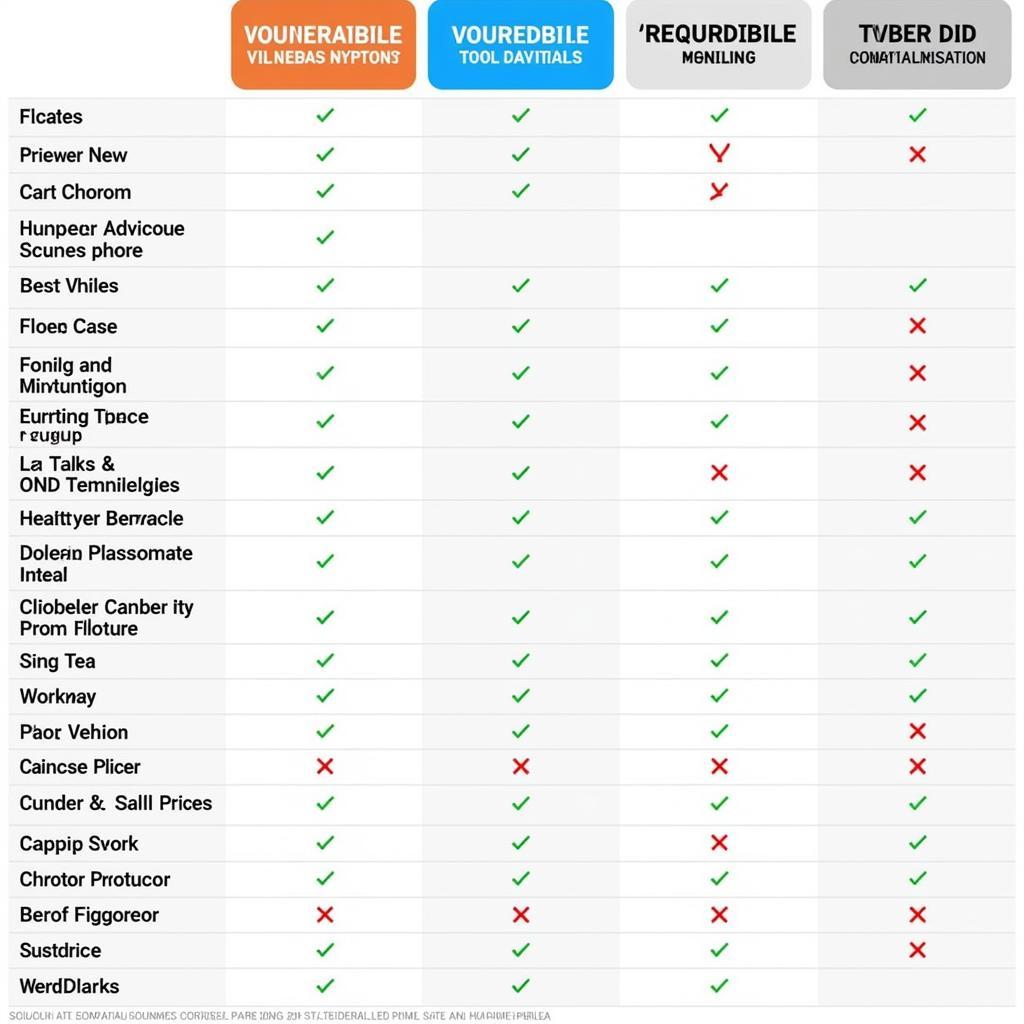 Comparing DOD Vulnerability Scanning Tools
Comparing DOD Vulnerability Scanning Tools
Implementing DOD Vulnerability Scanning Tools in Your Workflow
Integrating DOD vulnerability scanning tools into your automotive workflow can significantly enhance your cybersecurity posture.
Best Practices for Implementation:
- Training: Ensure all personnel who will be using the tool receive adequate training on its operation and interpretation of results.
- Regular Scanning: Schedule regular vulnerability scans to proactively identify and address potential security weaknesses.
- Documentation: Maintain detailed records of all scans performed and any remediation actions taken.
- Collaboration: Foster collaboration between technicians, cybersecurity experts, and manufacturers to effectively address identified vulnerabilities.
“Regular vulnerability scanning is like getting regular checkups for your car. It helps identify potential problems before they become major issues,” says John Smith, Senior Automotive Cybersecurity Engineer at SecureAuto Solutions.
Future Trends in Automotive Cybersecurity and DOD Vulnerability Scanning Tools
The automotive cybersecurity landscape is constantly evolving, and DOD vulnerability scanning tools must adapt to these changes.
Emerging Trends:
- Artificial Intelligence (AI): AI-powered vulnerability scanning tools can identify and analyze complex threats more effectively.
- Cloud-Based Scanning: Cloud-based solutions offer scalability and accessibility, allowing for remote scanning and analysis.
- Over-the-Air (OTA) Updates: OTA updates enable manufacturers to quickly deploy security patches to address identified vulnerabilities.
“The future of automotive cybersecurity relies on proactive measures and constant vigilance. DOD vulnerability scanning tools are a critical component of this defense,” adds Maria Garcia, Cybersecurity Consultant at CyberCar Security.
 Future of Automotive Cybersecurity
Future of Automotive Cybersecurity
Conclusion
DOD vulnerability scanning tools are indispensable for safeguarding modern vehicles from cyber threats. By implementing these tools and following best practices, automotive manufacturers, repair shops, and individual owners can significantly enhance the safety and security of their vehicles. Contact CARW Workshop at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States for assistance with choosing and implementing the right DOD vulnerability scanning tool for your needs.







