Docker Image Scanning Tools are essential for maintaining the security and integrity of your containerized applications. In today’s fast-paced development environment, ensuring your Docker images are free from vulnerabilities is crucial for protecting your systems and data. Using these powerful tools, you can identify and mitigate security risks early in the development lifecycle. docker images scanning tools are becoming increasingly important as more and more organizations adopt containerization.
Why are Docker Image Scanning Tools Important?
Docker images often incorporate numerous third-party libraries and dependencies, each potentially containing hidden vulnerabilities. Without proper scrutiny, these vulnerabilities can expose your applications to attacks. Docker image scanning tools automate the process of identifying these weaknesses, allowing you to address them before deployment. This proactive approach significantly reduces the risk of security breaches and ensures the stability of your containerized environments.
 Docker Image Scanning Process
Docker Image Scanning Process
How do Docker Image Scanning Tools Work?
These tools typically analyze the layers within a Docker image, comparing the contents against known vulnerability databases. They identify outdated software packages, insecure configurations, and other potential security risks. The tools then generate reports detailing the discovered vulnerabilities, often providing remediation advice. Some advanced tools also integrate with CI/CD pipelines, automating security checks throughout the development process.
Integrating Docker Image Scanning into Your Workflow
Integrating docker image scanning into your development workflow is crucial for proactive security. By incorporating scanning early, preferably during the build stage, you can identify vulnerabilities before they reach production. This early detection enables developers to address issues quickly and efficiently, minimizing the impact on the development cycle.
Choosing the Right Docker Image Scanning Tool
The best docker image vulnerability scanning tools for your needs will depend on factors such as the size of your organization, your budget, and your specific security requirements. Some popular options include open-source tools like Clair and Anchore Engine, as well as commercial solutions like Snyk and Aqua Security. Consider factors like ease of integration, reporting capabilities, and the comprehensiveness of the vulnerability database when making your decision.
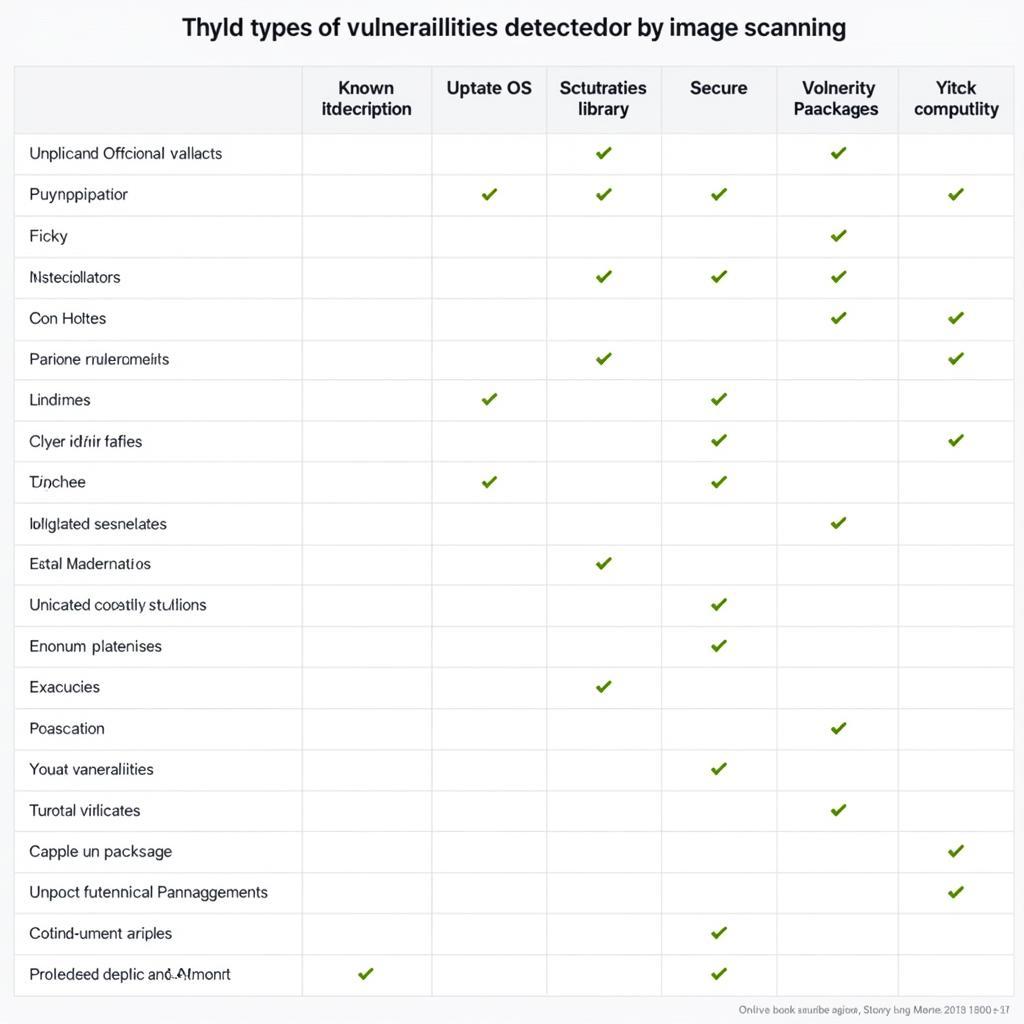
 Comparing Docker Image Scanning Tools
Comparing Docker Image Scanning Tools
“Regularly updating your vulnerability database is just as important as using a good scanning tool. Outdated databases can miss new threats, leaving your systems exposed,” advises John Smith, Senior Cybersecurity Consultant at SecureContainers Inc.
Open-Source vs. Commercial Docker Image Scanning Tools
While image scanning tools offer cost-effectiveness and community support, commercial solutions often provide advanced features, dedicated support, and broader vulnerability coverage. Choosing between open-source and commercial depends on your specific needs and resources. Open-source tools may be sufficient for smaller projects, while larger organizations might benefit from the robust features and support offered by commercial solutions.
What about Docker Container Scanning Open Source Tools?
You might also be interested in exploring docker container scanning open source tool comparison blog for a deeper dive into the available options. This provides valuable insights into their respective strengths and weaknesses.
“Don’t just scan your images once and forget about it. Regular scanning, ideally integrated into your CI/CD pipeline, is crucial for maintaining continuous security,” reminds us Maria Garcia, Lead DevOps Engineer at Containerized Solutions Ltd.
Best Practices for Using Docker Image Scanning Tools
To maximize the effectiveness of your container image scanning tools, implement these best practices:
- Scan early and often, integrating scanning into your CI/CD pipeline.
- Keep your vulnerability database up-to-date.
- Establish a process for addressing identified vulnerabilities promptly.
- Prioritize vulnerabilities based on severity and potential impact.
- Monitor and analyze scan results regularly to identify trends and improve your security posture.
Conclusion
Docker image scanning tools are indispensable for ensuring the security of your containerized applications. By proactively identifying and mitigating vulnerabilities, these tools help protect your systems and data from potential threats. Choosing the right tool and implementing best practices will significantly strengthen your container security posture. For expert assistance and tailored solutions, connect with us at CARW Workshop. You can reach us at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States. We’re here to help you navigate the complexities of container security and optimize your Docker image scanning processes. Don’t wait for a security breach to act—secure your containers today with docker image scanning tools.