Cloud Security Scanning Tools are essential for maintaining a secure cloud environment. They help identify vulnerabilities and misconfigurations that could lead to data breaches and other security incidents. This guide explores the world of cloud security scanning tools, helping you choose the right solutions for your needs. Learn how these tools work, their benefits, and how to implement them effectively. azure security scanning tools provide a robust solution for Microsoft Azure environments.
Understanding Cloud Security Scanning Tools
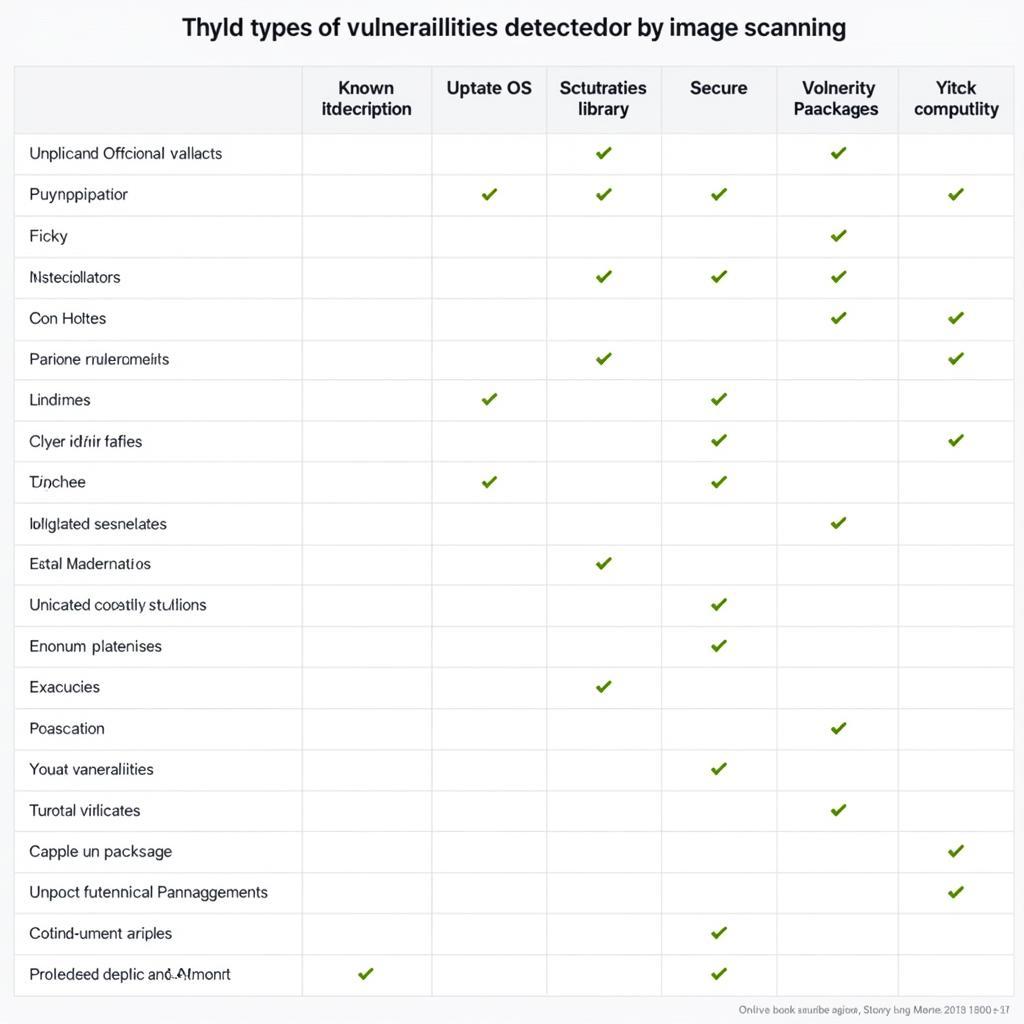
Cloud security scanning tools automate the process of identifying security risks in your cloud infrastructure. These tools analyze various aspects of your cloud setup, including virtual machines, networks, and applications, searching for potential vulnerabilities. They come in different forms, each with its own strengths. Some focus on specific cloud providers like AWS or Azure, while others offer more general capabilities.
What makes a good cloud security scanning tool? Accuracy, comprehensive coverage, and ease of use are key factors to consider. Look for tools that integrate seamlessly with your existing cloud environment and provide actionable insights.
Types of Cloud Security Scanning Tools
Vulnerability Scanners
These tools search for known vulnerabilities in your software and systems. They compare your cloud environment against a database of vulnerabilities and alert you to any matches. Regularly updating the vulnerability database is crucial for effective threat detection.
Configuration Scanners
Configuration scanners assess your cloud environment for misconfigurations. They check for compliance with security best practices and identify any deviations from established standards. These tools are essential for ensuring your cloud setup adheres to industry regulations and internal policies.
Penetration Testing Tools
Penetration testing tools simulate real-world attacks to identify vulnerabilities that could be exploited by malicious actors. These tools provide a more proactive approach to security by testing your defenses before actual attacks occur.
Choosing the Right Cloud Security Scanning Tools
Selecting the right tools depends on your specific needs and cloud environment. Consider factors like the size of your infrastructure, the complexity of your applications, and your budget. docker container scanning open source tool comparison blog provides valuable insights for those working with containerized environments.
Do you primarily use Azure? If so, then exploring azure stack scanning tools might be your best bet. For a broader perspective, reviewing the top 10 vulnerability assessment scanning tools can be beneficial.
What are the costs associated with these tools? Many vendors offer different pricing models, from subscription-based services to one-time purchases.
Implementing Cloud Security Scanning Tools
Integrating these tools into your workflow should be seamless. Automate the scanning process to ensure regular checks. Schedule scans to run at specific intervals, such as daily or weekly, and configure alerts to notify you of any critical vulnerabilities.
“Regular scanning and prompt remediation are crucial for maintaining a strong security posture in the cloud,” says Alex Thompson, Senior Cloud Security Architect at SecureCloud Solutions.
Conclusion
Cloud security scanning tools are indispensable for protecting your cloud infrastructure. By implementing the right tools and strategies, you can significantly reduce your risk of security breaches and maintain a secure cloud environment. Remember to choose tools that align with your specific needs and integrate them seamlessly into your existing workflows. For further assistance or tailored solutions, connect with CARW Workshop at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States. We’re ready to help you enhance your cloud security with the right cloud security scanning tools.
“Don’t wait for a breach to happen. Proactive security measures are the best defense,” adds Maria Sanchez, Cybersecurity Consultant at CyberSafe Solutions.
FAQ
- What is the difference between vulnerability scanning and penetration testing?
- How often should I run cloud security scans?
- What are the benefits of using automated cloud security scanning tools?
- How do I choose the right cloud security scanning tools for my business?
- What are some best practices for implementing cloud security scanning tools?
- How much do cloud security scanning tools cost?
- Can cloud security scanning tools integrate with my existing security systems?




One Response