Many of us rely on Bluetooth connectivity daily, whether it’s for hands-free calls in our cars or connecting devices to our Macs. This convenience raises questions about security, especially concerning Car Bluetooth Scanners and devices that might attempt to detect or access our sleeping computers. A common concern is whether a car Bluetooth scanner, or any Bluetooth scanner for that matter, could detect a Mac that is in sleep mode. Let’s delve into this question and explore the possibilities.
Initially, one might assume that a sleeping Mac would be invisible to Bluetooth scanners. This aligns with the idea that devices need to be in a discovery or “pairing” mode to be detected. As Allan suggested, the logic points towards a sleeping Mac being undetectable.
[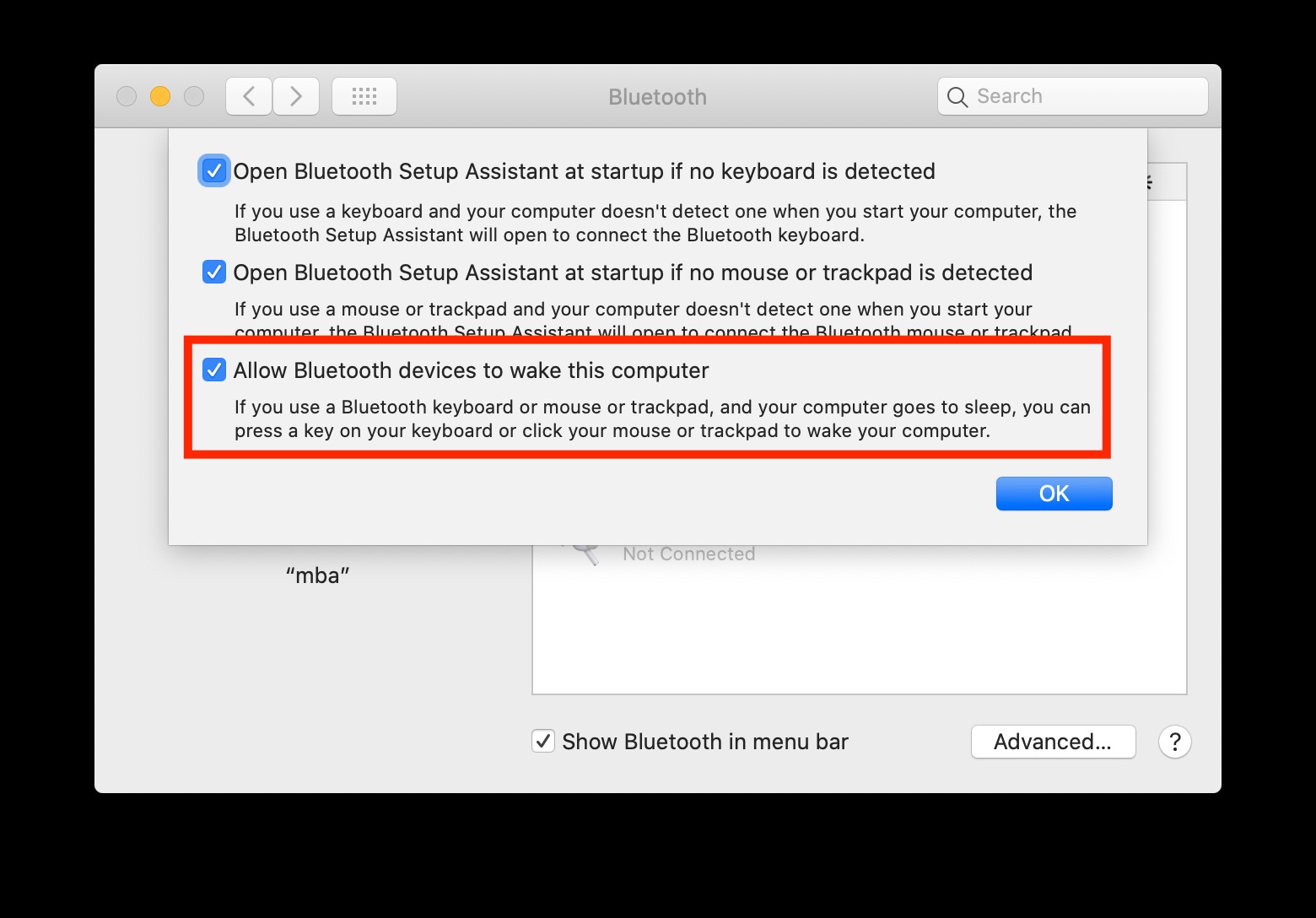 Screenshot of Bluetooth Advanced](Bluetooth Advanced Settings)
Screenshot of Bluetooth Advanced](Bluetooth Advanced Settings)
However, macOS has a setting in System Preferences » Bluetooth » Advanced labeled “Allow Bluetooth devices to wake this computer,” which is enabled by default. This setting prompts us to consider if a sleeping Mac might still be broadcasting or listening for Bluetooth signals, potentially making it detectable by a car Bluetooth scanner or similar tools.
The descriptive text for this setting clarifies that it’s intended for use with keyboards, mice, and trackpads that are already paired with the Mac. This suggests it might not extend to general Bluetooth scanners, including car Bluetooth scanners, attempting to initiate a new connection or detection.
The core of the uncertainty lies in understanding how car Bluetooth scanners and similar devices operate. The fundamental question remains: how do these Bluetooth scanners really work? Without a clear understanding of their detection mechanisms, it’s difficult to definitively say whether they can identify a sleeping Mac.
Is there a car Bluetooth scanner or any tool capable of detecting a Bluetooth signal from a Mac in sleep mode? Providing a definitive “no” with absolute certainty is challenging without deeper knowledge of scanner capabilities.
For those seeking complete assurance that their sleeping Mac remains invisible to car Bluetooth scanners or any Bluetooth detection attempts, the most reliable solution is to ensure Bluetooth is completely disabled when the Mac enters sleep mode.
One effective method to achieve this involves using automation tools like Keyboard Maestro in conjunction with the command-line tool blueutil. By creating a macro in Keyboard Maestro that triggers when your Mac goes to sleep, you can automatically disable Bluetooth.
[](Keyboard Maestro Macro for Bluetooth Control)
To implement this, you would need to install blueutil. Then, configure Keyboard Maestro to execute the command /usr/local/bin/blueutil --power 0 --discoverable 0 when your Mac sleeps. This command effectively turns off the Bluetooth radio and disables discoverability, providing a high level of confidence that no car Bluetooth scanner or similar device can detect your Mac.
For users who regularly utilize Bluetooth, a complementary Keyboard Maestro macro can be set up to run upon waking the Mac. This macro can re-enable Bluetooth with the command /usr/local/bin/blueutil --power 1 or reinstate both Bluetooth and discoverability with /usr/local/bin/blueutil --power 1 --discoverable 1.
While initial reasoning and expert opinions, like Allan’s, suggest that sleeping Macs should be undetectable, the lack of comprehensive knowledge about the full capabilities of car Bluetooth scanners and similar tools leaves room for uncertainty. Therefore, for users prioritizing absolute privacy and security against Bluetooth detection when their Mac is sleeping, actively disabling Bluetooth using tools like Keyboard Maestro and blueutil offers the most robust solution.
Update: Further insights, such as those referenced from MacEnthusiasts.com, reinforce the likelihood that Bluetooth is indeed powered off when a Mac’s lid is closed, potentially making the Keyboard Maestro macros redundant in many modern scenarios. However, historical experiences of MacBooks waking up in bags due to Bluetooth device interactions remind us that past behavior might not always reflect current configurations. Whether these past experiences are outdated remains a point to consider.

