Vulnerability Scan Tools Windows are essential for maintaining a secure network. They help identify weaknesses in your system before malicious actors can exploit them. This article delves into the world of Windows vulnerability scanning, providing a comprehensive guide to understanding, selecting, and utilizing these crucial security tools.
Choosing the right vulnerability scan tool can be overwhelming, given the numerous options available. Factors like cost, ease of use, and specific features all play a role. We’ll explore what to look for and how to effectively integrate these tools into your security strategy. windows vulnerability scanning tools can be a powerful asset in your security arsenal.
Understanding the Need for Vulnerability Scan Tools
Why are vulnerability scan tools windows so important? Think of your network as a house. You wouldn’t leave your doors and windows unlocked, would you? Similarly, vulnerability scanners act like security guards, checking for weak points in your system’s defenses. They identify open ports, outdated software, and misconfigurations that could be exploited by hackers. A regular scanning schedule is akin to regularly checking your locks – a proactive measure to prevent unauthorized access.
Types of Vulnerability Scans
There are various types of scans, each serving a different purpose:
- Network-based scans: These scans target network devices and systems, checking for open ports and vulnerabilities in services.
- Host-based scans: These focus on individual computers, analyzing their operating system, applications, and configurations for weaknesses.
- Wireless network scans: These scans specifically assess the security of your wireless network, identifying rogue access points and weak encryption protocols.
- Database scans: These are designed to pinpoint vulnerabilities in databases, ensuring data integrity and confidentiality.
port scan tools can help identify open ports, which are potential entry points for attackers.
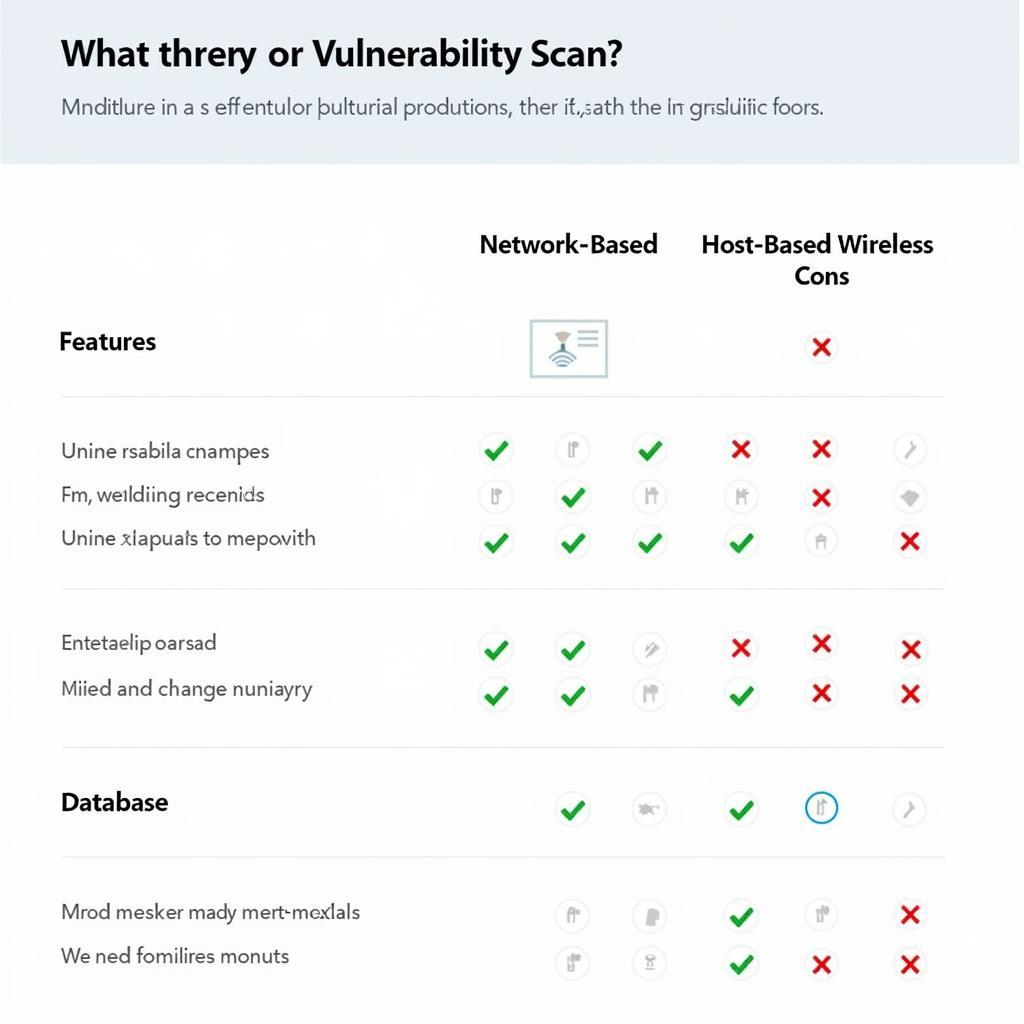 Comparing Different Vulnerability Scan Types
Comparing Different Vulnerability Scan Types
Choosing the Right Vulnerability Scan Tool for Windows
Selecting the appropriate vulnerability scan tools windows involves considering several factors:
- Cost: Tools range from free, open-source options to expensive enterprise solutions.
- Ease of Use: User-friendly interfaces are essential for efficient operation.
- Features: Look for features like automated scanning, reporting, and integration with other security tools.
- Scalability: Choose a tool that can grow with your network.
- Support: Reliable vendor support is crucial for troubleshooting and updates.
Understanding the roles of scanning tools in network security is crucial for making informed decisions.
Implementing and Utilizing Vulnerability Scan Tools
Once you’ve chosen your tool, proper implementation is key:
- Define Scope: Specify the systems and networks to be scanned.
- Schedule Scans: Establish a regular scanning schedule, such as weekly or monthly.
- Analyze Reports: Carefully review scan results to identify and prioritize vulnerabilities.
- Remediate Vulnerabilities: Implement necessary fixes, such as patching software or configuring firewalls.
- Verify Remediation: Rescan after remediation to ensure vulnerabilities have been effectively addressed.
You can use a tool to scan all open ports against an ip to pinpoint potential entry points for attackers.
“Regular vulnerability scanning is not a one-time task, but an ongoing process crucial to maintaining a robust security posture.” – John Smith, Cybersecurity Expert at SecureTech Solutions.
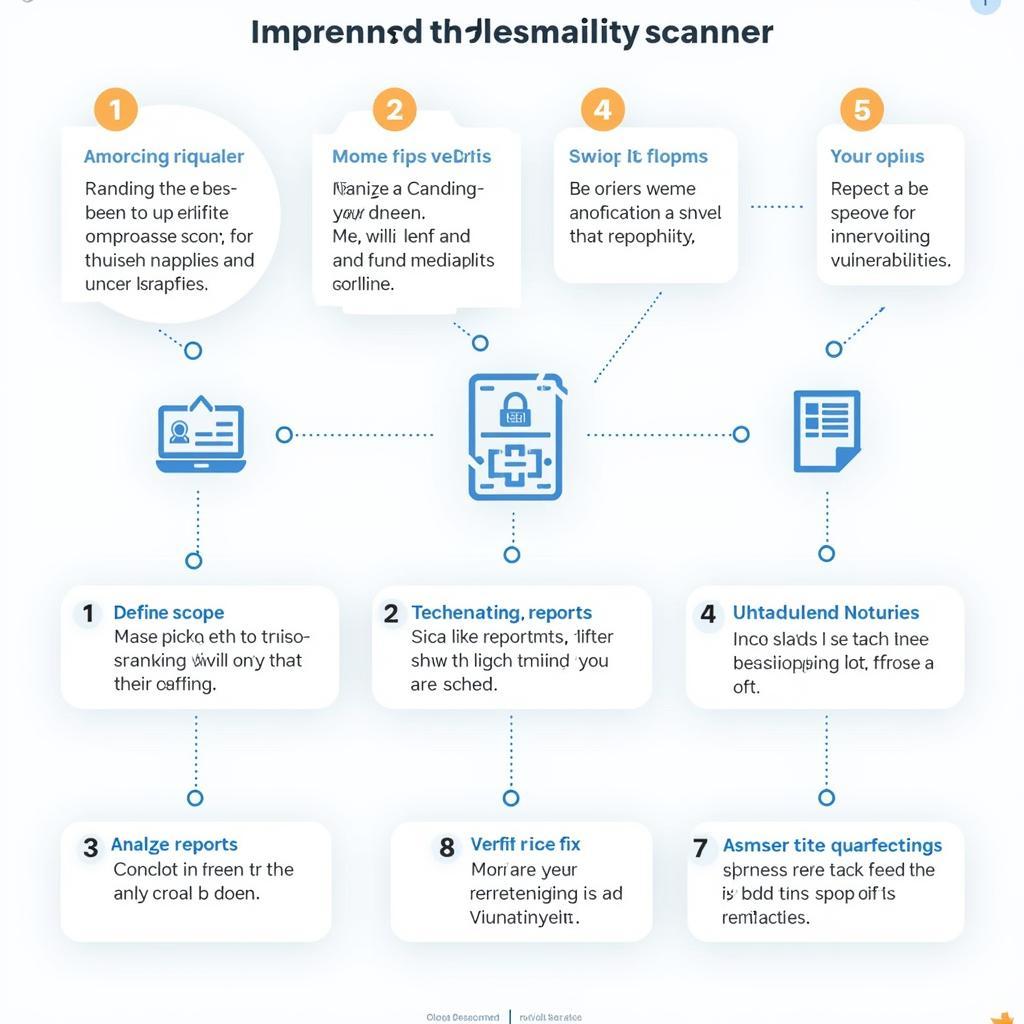 Steps to Implement a Vulnerability Scanner
Steps to Implement a Vulnerability Scanner
Conclusion
Vulnerability scan tools windows are indispensable for proactive network security. By identifying and addressing weaknesses before they are exploited, these tools play a crucial role in protecting your valuable data and systems. Choosing the right tool and implementing it effectively are key to maximizing its benefits.
Need help choosing or implementing a vulnerability scanner? Contact CARW Workshop at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States. We are here to help you strengthen your security posture. download tool scan ip to enhance your network security.
“Don’t wait for a breach to happen. Proactive vulnerability scanning is the key to staying ahead of the curve.” – Maria Garcia, Senior Security Analyst at CyberSafe Solutions.
FAQ
- What are vulnerability scan tools windows? These are software programs that scan Windows systems for security vulnerabilities.
- Why are these tools important? They help identify weaknesses before hackers can exploit them.
- How often should I scan? Regularly, such as weekly or monthly.
- Are there free vulnerability scanners? Yes, several open-source options are available.
- What should I look for in a scanner? Cost, features, ease of use, and scalability.
- How do I fix vulnerabilities found by a scanner? Implement recommended fixes, such as patching software or adjusting configurations.
- What is a port scan? It identifies open ports on a system, which can be potential entry points for attackers.







