Application scanning tools are crucial for identifying vulnerabilities that could expose sensitive information. These tools automate the process of checking for security flaws, helping organizations protect their data and maintain compliance. From simple port scanners to sophisticated API analysis tools, understanding the landscape of application scanning is essential in today’s digital world. Learn how these tools can safeguard your valuable data.
Why Use Application Scanning Tools to Check Sensitive Information?
Data breaches are a constant threat, and protecting sensitive information is paramount. Application scanning tools provide a proactive approach to security, identifying vulnerabilities before they can be exploited. These tools can scan various aspects of an application, from the network layer to the application logic, ensuring comprehensive coverage. tools scan website offer a robust solution for identifying vulnerabilities across your web applications.
Different Types of Application Scanning Tools
Various types of application scanning tools cater to different needs. Static Application Security Testing (SAST) analyzes the source code without executing the application. Dynamic Application Security Testing (DAST) tests the running application, simulating real-world attacks. Software Composition Analysis (SCA) identifies vulnerabilities in open-source components. Choosing the right tool depends on your specific requirements and the nature of your application.
“Choosing the right application scanning tool is like choosing the right lock for your door. You need to understand the threats you face and the level of protection you require,” says John Smith, Cybersecurity Expert at SecureTech Solutions.
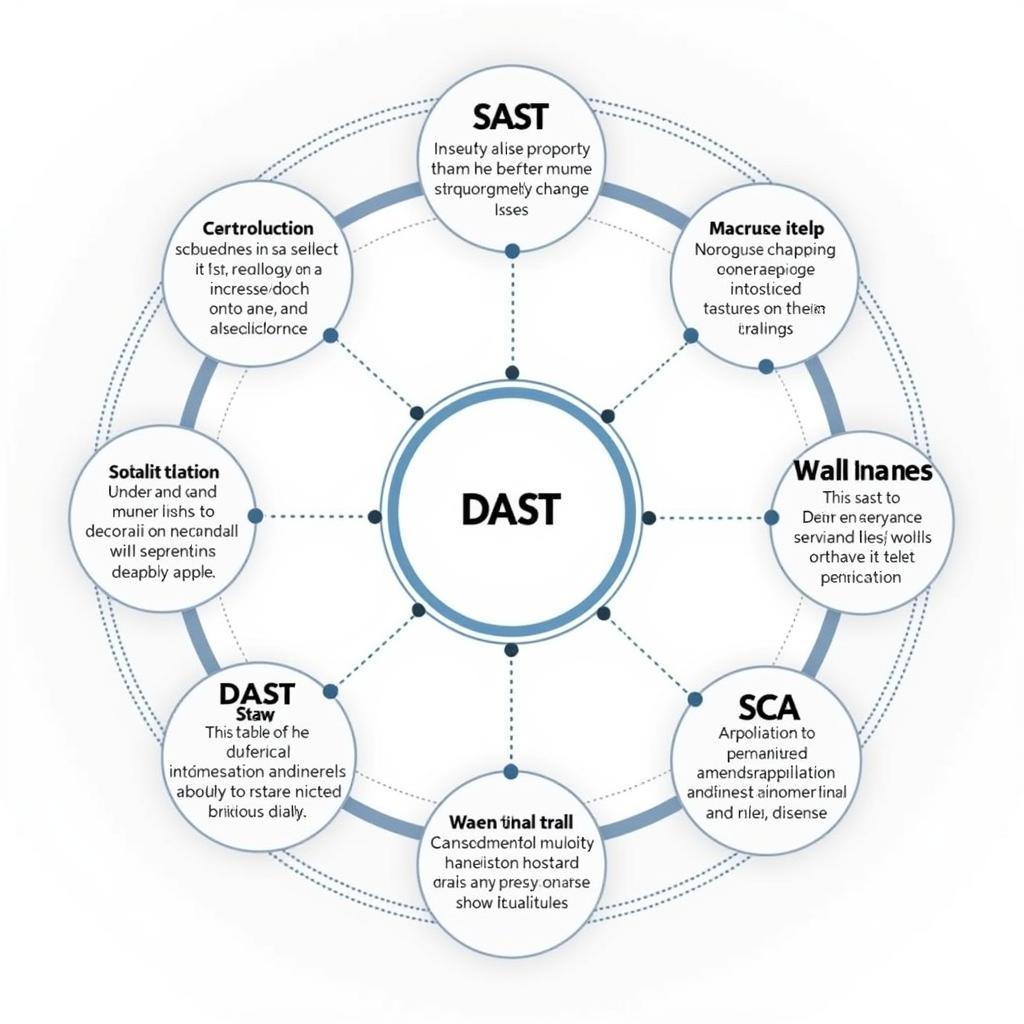 Types of Application Scanning Tools
Types of Application Scanning Tools
How to Effectively Use Application Scanning Tools
Effective use of application scanning tools requires a structured approach. First, define the scope of the scan, identifying the specific applications and systems to be tested. Next, configure the tool appropriately, selecting the relevant scanning parameters. Regularly scan your applications, ideally integrating the scanning process into your development pipeline. api vulnerability scanning tools are essential for modern web applications that rely heavily on APIs.
Interpreting Scan Results and Remediation
After scanning, analyze the results carefully. Prioritize vulnerabilities based on their severity and potential impact. Develop a remediation plan to address the identified issues. Regularly monitor your applications to ensure that vulnerabilities are fixed promptly and effectively.
 Analyzing Application Scanning Results
Analyzing Application Scanning Results
What are the benefits of using application scanning tools?
Application scanning tools offer numerous benefits, including early vulnerability detection, reduced security risks, and improved compliance. They also save time and resources by automating the security testing process. remote port scanning tool can quickly identify open ports on your network, helping you understand potential entry points for attackers.
“Regular application scanning is not just a best practice, it’s a necessity in today’s interconnected world. It’s like getting regular check-ups for your car – it prevents small problems from becoming major headaches,” says Maria Garcia, Senior Security Consultant at CyberSafe Solutions.
Choosing the Right Application Scanning Tools to Check Sensitive Information
Selecting the appropriate application scanning tool requires careful consideration. Evaluate the tool’s features, ease of use, and integration capabilities. Consider your budget and the level of support provided by the vendor. pci compliance scan tools are essential for businesses that handle credit card information. Choosing the right tool can significantly enhance your organization’s security posture. network scanning & hacking tools can help you identify vulnerabilities in your network infrastructure.
Conclusion
Application scanning tools are essential for protecting sensitive information in today’s increasingly complex digital landscape. By using these tools effectively, organizations can proactively identify and address vulnerabilities, minimizing the risk of data breaches and ensuring compliance. Remember to choose the right tools, implement them correctly, and consistently monitor your applications for optimal security. For expert assistance and tailored solutions, connect with us at CARW Workshop. You can reach us at +1 (641) 206-8880 or visit our office at 4 Villa Wy, Shoshoni, Wyoming, United States.
FAQ
- What is the difference between SAST and DAST?
- How often should I scan my applications?
- What are the common vulnerabilities found by application scanning tools?
- How can I integrate application scanning into my development process?
- What is the cost of application scanning tools?
- Can application scanning tools prevent all security breaches?
- How can I choose the best application scanning tool for my needs?





One Response